Did you know that sipp can play back RTP streams? A lot of long time users may not!
Did you know that you can use Wireshark to extract a RTP stream sipp can use for that playback? Together these form a quite powerful tool for testing audio!
So how do you do it? Well, we need to start with a packet capture of a SIP call including RTP. If you don’t have one, go ahead and fire up Wireshark or tcpdump or any other packet capture software and your favorite SIP client and capture the call.
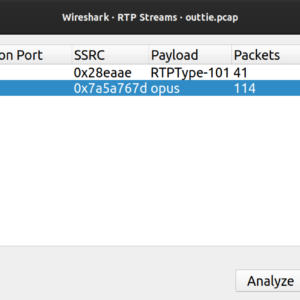
Once you have it, go ahead and open it up in Wireshark. From the top menu select: Telephony, RTP, RTP Streams. That should leave you with a window like this:
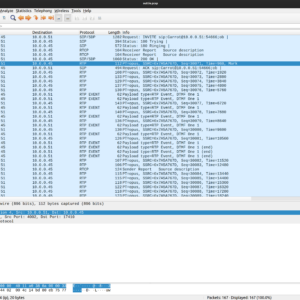
From there you want to select “Prepare Filter”. If we did this correctly your packet capture should go from looking like this:
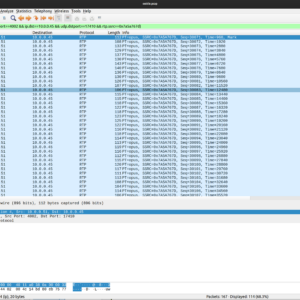
To looking like this:
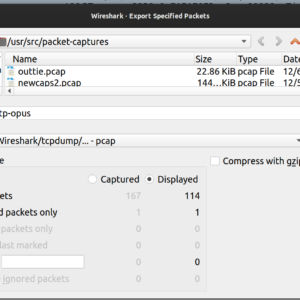
As you can see, we are now only displaying the packets for that stream. From here, select from the top menu, File then Export Specified Packets… Once you do, make sure that All Displayed packets are set as shown here, then go ahead and save:
Now we have a packet capture that contains just the RTP stream we can use for playback in sipp.
Before we can start playback, make sure that your installed version of sipp was compiled with this capability.
From there it is a matter of adding a call to pcap_play_audio pointing to your RTP capture at the correct place in your scenario file:
<nop>
<action>
<exec play_pcap_audio="rtp-opus.pcap"/>
</action>
</nop>And that’s it! Your scenario will now send the RTP stream to the remote location negotiated in the SDP. Note that sipp is just re-sending the existing audio, so the format contained in the capture needs to match the SDP in the scenario to be valid.
You can use this functionality in a UAS or UAC scenario, or even at both ends to test audio in both directions!
The post Debugging RTP with sipp and Wireshark appeared first on Asterisk.
Source link




No Comment! Be the first one.